Introduction:
SonarQube (formerly Sonar) is an open-source platform developed by SonarSource for continuous inspection of code quality to perform automatic reviews with static analysis of code to detect bugs, code smells, and security vulnerabilities on 20+ programming languages.
Lets directly jump into installation and Configuration for a java based application.
Step 1: Download Sonarqube from the link below https://binaries.sonarsource.com/Distribution/sonarqube/sonarqube-7.8.zip
Note 1: Above is the last major supported version for java 8 and use the 7.x version only to ensure your sonarqube application runs properly.
Note 2: You will face weird errors if you dont check for version compatibility and so request you to please check with your version compatibility against java.
Step 2: After download, extract to a folder as required on your file system and start the server as below to test.
Step 3: Add the below lines in maven m2 settings.xml or in your parent pom of the project.
For Example, see below
<settings>
<pluginGroups>
<pluginGroup>org.sonarsource.scanner.maven</pluginGroup>
</pluginGroups>
<profiles>
<profile>
<id>sonar</id>
<activation>
<activeByDefault>true</activeByDefault>
</activation>
<properties>
<!-- Optional URL to server. Default value is http://localhost:9000 -->
<sonar.host.url>
http://myserver:9000
</sonar.host.url>
</properties>
</profile>
</profiles>
</settings>Step 4: Go to your Sonarqube bin directory <SONAR_HOME>\bin and select your respective batch file to start sonarqube.
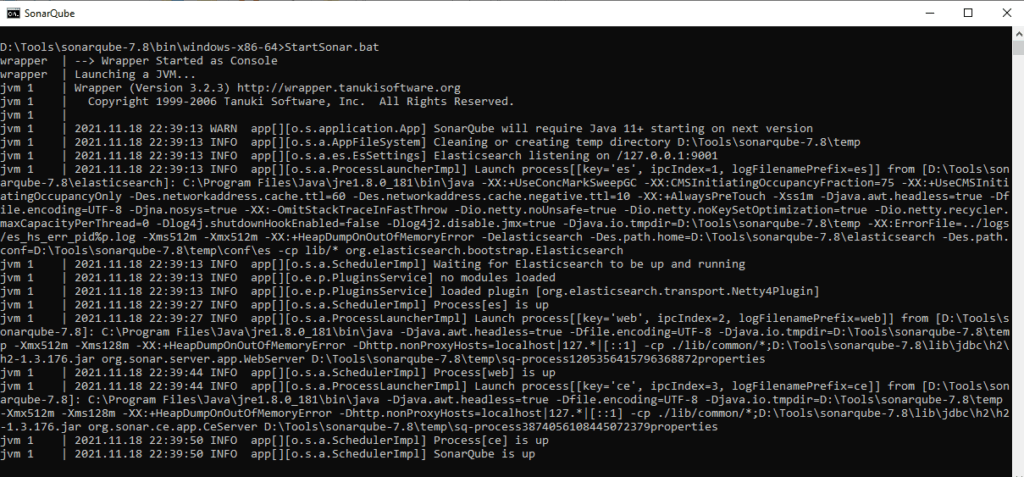
Step 5: If everything is configured properly as mentioned in above steps, you should see a similar output which says “SonarQube is up” as shown below.
Screenshot below for reference:
Step 6: Once it is up, now it is time to configure your Application to start using SonarQube. Please add the below dependency to your pom.xml to start using sonarqube in application.
<!-- https://mvnrepository.com/artifact/org.sonarsource.scanner.maven/sonar-maven-plugin -->
<dependency>
<groupId>org.sonarsource.scanner.maven</groupId>
<artifactId>sonar-maven-plugin</artifactId>
<version>3.7.0.1746</version>
</dependency>Step 7: Refresh the pom or update project to download the dependencies. Once it is downloaded, run the maven using the command below
maven sonar:sonarStep 8: More information can be found on the below reference sites to get more understanding.